Original Scientific Paper, Volume 23, Number 2, Year 2025, No 1280, pp 374-383
Received: Mar 10, 2025 Accepted: Jun 10, 2025 Published: Jun 16, 2025
DOI: 10.5937/jaes0-57511
SIMULATION OF THE MOBILE OBJECTS IDENTIFICATION PROCESSES IN THE SUPPLY CHAINS
Abstract
The paper considers the problem of choosing the optimal combination of identification technologies for a class of cyber-physical systems controlling technological (micro-logistics) processes, the specificity of which does not allow using the same identification method at all technological stages. The formal statement of the problem is presented. Criteria, constraints and conditions of search for optimal combinations of technologies are defined. The solution of the problem is considered on the example of the control system of mobile equipment turnover. The simulation model created for generation of full space of admissible variants of combinations of identification technologies, calculation of parameters, modeling of technological process execution and search of quasi-optimal solution is described. The model structure, main modules and functions are disclosed. The simulation model presented in this article generates the full space of admissible variants of identification technology combinations, performs parameter calculations, simulates technological process execution, and identifies quasi-optimal solutions. The model's structure, including its key modules and functions, is also described. The space of admissible configurations obtained from the simulation is analyzed. The results of the optimal solution search are presented, along with their dependence on the model's parameters and constraints.
Highlights
- Novel approach: Combines multiple identification technologies (RFID, Bluetooth, QR) for optimal micro-logistics automation in aircraft maintenance.
- Simulation model: Generates 28,800 valid configurations, evaluating automation level, cost, and reliability via colored Petri nets.
- Key findings: Identifies Pareto-optimal solutions, showing trade-offs between automation and implementation costs.
- Practical impact: Enables reliable tracking of mobile kitchen equipment (MOKE), reducing human error and manual paperwork in supply chains.
Keywords
Content
1 Introduction
Aircraft maintenance at an airport is a complex process that involves many services and a large number of technical facilities that coordinate their activities to fulfill the main task of ensuring the departure of an aircraft at a set time according to schedule. One of these processes is after–sales service, the purpose of which is to prepare for passenger service during the flight. Everything necessary for passengers in flight is transported and loaded on board in special metal containers of various types called mobile onboard kitchen equipment (MOKE) [1-2].
It is necessary to deploy a system for reliably detecting moving objects. The features and conditions of technological operations do not allow for individual accounting of the movement of MOKE units. The existing service technology involves the use of manual labor at all technological stages. The specifics of production make it impossible to automate the loading and unloading of MOKE. At the same time, all accounting operations are performed manually using statements and other paper documents. The lack of technology for automatic identification of MOKE units, due to historical reasons and technological features, leads to difficulties in accounting and controlling the movement of MOKE, making accounting impossible at some critical technological stages. The human factor influence is the reason that the data obtained is unreliable, irrelevant, and incomplete.
To improve the quality of aircraft goods delivery on board it is necessary to use the Mobile Equipment Turnover Control System (METCS). It solves the mobile equipment movement tracking (MEMT) problem through all stages of the technological (logistics) process of preparation, delivery and loading of everything necessary to serve passengers in flight.
However, the composition of the elements and functions of such a system may vary [3-7]. Identification methods used in the METCS system differ in several parameters. Possible combinations of identification technologies lead to a multitude of realization variants of the considered intelligent information system. In essence, the task of multicriteria structural and functional synthesis [8-9] must be solved. The optimal choice from the set of possible combinations of identification technologies (hereinafter referred to as configurations) is a multi-criteria selection problem requiring special methods of solution.
1.1 Literature review
The automatic object identification problem is widely known both in general formulation and in relation to transport and logistics systems [10-11].
Automatic identification methods are based on a number of well-known technologies: optical barcode recognition (2D, 3D, QR-code) [12-14]; Bluetooth and RFID Identification [15-16] and RFID [17-20].
There are restrictions imposed by airlines on the use of active tags on board aircraft during flight. Therefore, the report suggests choosing RFID technology as the base [21]. It has wide applications in the field of cargo movement and transport in ports, container terminals, warehouse logistics, and control in supply chains [22].
RFID has not been used before to label METCS for a number of reasons. Firstly, the MOKE is a metal box. Secondly, the transportation technology involves installing MOKE in close proximity to each other, in several rows in width and height, which generally leads to complete shielding of the radio frequency tag. To solve the problem of marking MOKE with an RFID tag, the authors of the article conducted research and tests of various types of tags, selected locations for installing tags on MOKE, developed an antenna installation system, and created a unique identification algorithm [23-24].
The analysis of various approaches to modeling and simulation METCS functioning showed that the authors emphasize the need for flexible, adaptive solutions to take into account a variety of factors and uncertainties. However, everyone faces certain computational or structural limitations. One way or another, the specialists selected technologies for the optimal creation of specific narrowly focused models aimed at describing a well-known process in advance. We, in turn, will use colored Petri nets, which are not inferior to the described solutions, but better suited to our tasks, provide a high level of flexibility, allow us to create a visual model describing the work of each individual part, and are undemanding to resources [25].
1.1 Formal problem statement
Within the framework of the MOKE TCS, a set of identification methods and technologies is considered (Table 1), for which the automation level coefficients are determined.
Table 1. Coefficients of the automation
| No. | Identification type and the method that implements it | TID | V |
| 1. | Manual identification by operator | total count | 1 |
| a list check for each unit | 1 | ||
| 2. | Semi-automatic identification | optical barcode scanning (QR-code) | 2 |
| scanning by handheld scanner of NFC tags and loggers for each MOKE unit | 2 | ||
| scanning with a handheld RFID tag scanner for a MOKE unit or group | 3 | ||
| Bluetooth handheld scanner scanning of tags for a MOKE unit or group | 3 | ||
| 3. | Automatic identification | scanning by the RFID tag scanner system for a MOKE unit crossing the zone boundary. | 4 |
| scanning by the system of Bluetooth tag readers for a MOKE unit located in a certain zone. | 4 |
For the subject area under consideration, we introduce sets and relations on them.
$A=\left\{a_1,\ a_2,\ldots,a_n\right\}$ is a set of information technologies of identification (TID) of mobile equipment (MOKE);
$V=\left\{v_1,\ v_2,\ldots,v_n\right\}$ set of coefficients reflecting the level of automation of identification technology ai;
$L=\left\{1,\ldots,k\right\}$ a set of numbers of stages in the technological process of aircraft maintenance service;
$K=\left\{k_1,\ k_2,\ldots,k_k\right\}$ set of coefficients reflecting the minimum required level of automation at the stages 1-k;
$B = \{ b_1^l,\, b_2^l,\, \ldots,\, b_m^l \}$ set of resources, on which information identification technologies are realized at the l-stage of the technological process;
The model considers the following set of resources: operator (typified by process steps); handheld optical industrial scanner; handheld RFID industrial scanner; handheld industrial NFC scanner; household cell phone as an optical, NFC and Bluetooth scanner; stationary RFID scanner; stationary RFID tag scanning equipment system; stationary Bluetooth tag scanning equipment system; RFID tag identification system on mobile vehicle.
$S = \left\{s_1,\, s_2,\, \ldots,\, s_\rho\right\}$ set of mobile equipment Meq;
$D=\left\{d_{ij}^{<p,l>}\right\}$ set of coefficients characterizing the reliability of identification of mobile equipment Sp at the l-stage of the technological process using ai -technology implemented on bj resource. They are determined by experts and are in the range $0{<d}_{ij}^{<p,l>}<1$
$C=\left\{c_{ij}^{<p,l>}\right\}$ set of coefficients characterizing at l-stage the costs of implementing ai identification technology on bj resource. They are determined by experts based on the total cost of ownership and labor costs for the identification operation at each stage.
$T=\left\{t_{ij}^{<p,l>}\right\}$ a set of coefficients characterizing time costs for identification of a unit of mobile equipment Sp at the l-stage of the technological process using ai -technology implemented on bj resource.
$W^l=$$w_1^l,\, w_2^l,\, \ldots,\, w_m^l$ set of coefficients, reflecting allowable time constraints for identification of mobile equipment at the stage l.
The applicability function of the identification method at the stage, determines the possibility of using TID:
| $\text{eps}(i, l) = \begin{cases} 1, & \text{if } a_i \text{ is TID at stage } l \\ 0, & \text{otherwise} \end{cases}$ | (1) |
Let's introduce the variables:
| $x_{ij}^{< p, l >} = \begin{cases} 1, & \text{if } a_i \text{ TID is implemented at resource } b_j \\ & \quad \text{at stage } l \text{ during identification, } S_p \subset S_0 \\ 0, & \text{otherwise} \end{cases}$ | (2) |
In order to find variants of the optimal solution, it is required to maximize the number of stages in which the automation of Meq identification processes is carried out, increasing the level of automation and minimizing the total cost of complex automation. We use a combined method - operator solving rule and concession method [26].
For each step l, a function specifying the level of automation is defined:
| $F_l(X) = \sum_{i \in A} \sum_{j \in B} \sum_{p \in S} v_i \cdot \text{eps}(i,j) \cdot x_{ij}^{< p, l >} \geq w$ | (3) |
where w is the lower boundary of the level of automation at all stages of the technological process, which is determined taking into account the constraints on the minimum required level of automation at each stage l –k_l\ ⸦ K
The cost function is defined as:
| $w\geq\ \ k_l\ \forall l$ | (4) | |
| $C(X) = \sum_{i \in A} \sum_{j \in B} \sum_{l \in L} \sum_{p \in S} \text{eps}(i, j) \cdot c_{ij}^{<p, l >} \cdot x_{ij}^{< p, l >}$ |
The problem of finding an optimal solution is formulated as follows:
$w\rightarrow{\max}$ maximizing the overall level of automation;
$F_1(X) \geq w,\quad F_2(X) \geq w,\quad \ldots,\quad F_l(X) \geq w$ for all stages l ⸦ L;
$C(X) \leq \Delta_1 + q \cdot \bigl(C, \ldots \bigr)$ Let \( \Delta_1 \) be the cost threshold, \( C \) the concession value, and \( q \) the number of required solutions from the Pareto domain, then
X ⸦ $\Delta_X$ admissible set of combinations of identification technologies, depending on the chosen value of concession q*$\Delta C$
At the same time, it is necessary to ensure the fulfillment of restrictions, firstly, on the level of reliability, and, secondly, on the time of identification operations.
The required level of identification confidence for the entire configuration and at individual stages can be defined as follows:
Nl total number of objects identified at the l-th stage using applicable technologies and available resources.
The number of correctly identified objects at the l-th stage:
| $N_l = \sum_{i \in A} \sum_{j \in B} \sum_{p \in S} \text{eps}(i,j) \cdot x_{ij}^{\langle p, l \rangle}$ | (5) | |
| Reliability of object identification at the l-th stage: | ||
| $N_l^{+} = \sum_{i \in A} \sum_{j \in B} \sum_{p \in S} \text{eps} (i,j) \cdot d_{ij}^{\langle p, l \rangle} \cdot x_{ij}^{\langle p, l \rangle}$ | (6) | |
| $D_l = \frac{N_l^{+}}{N_l}$ | (7) |
Reliability of object identification at all stages of identification:
$D = \frac{\sum_{l \in L} N_l^{+}}{N_k}$ where $N_k$ - number of stages in the configuration under consideration.
Reliability of object identification at all stages of identification:
where - number of stages in the configuration under consideration.
The required level of reliability for identification is defined as $D \geq \Delta_2$ – for all stages and/or for each stage $l D_l \geq \Delta_2^l - l, \quad \forall l$
Limitations on the total time spent on Sp identification at the l-stage of the technological process:
| $\sum_{i \in A} \sum_{j \in B} \sum_{p \in S} t_{ij}^{\langle p, l \rangle} \cdot \varepsilon(i, j) \cdot x_{ij}^{< p, l >} \leq w_l, \quad \forall l$ | (8) |
The total automation factor for the optimal configuration can be calculated using the following formula:
| $K_{\text{auto}} = \sum_{l \in K} \sum_{i \in A} \sum_{j \in B} \sum_{p \in S} v_i \cdot \text{eps}(i, j) \cdot x_{ij}^{< p, l >}$ | (9) |
If $ K^1_{\text{auto}}$ corresponds to the initial state of the system, and is calculated for the system configuration obtained as a result of solving the optimization problem, the automation gain factor is calculated as follows:
| $K_a = \frac{K^{j}_{\text{auto}}}{K^{i}_{\text{auto}}}$ | (10) |
2 Materials and methods
2.1 Simulation model description
The whole process of a service enterprise is complex and can be represented as a set of parallel subprocesses. One sub-process was selected for modeling - preparation for departure.
MOKE is delivered to the aircraft using specialized transport and technological means (autolifts). The autolifts operate in parallel and participate in the realization of three technological stages. The number of autolifts used simultaneously is a configuration parameter. Distribution of MOKE on autolifts, according to the distribution formula obtained by expert method. The description of the process in the CPN TOOLS labeled Petri nets environment is given below (Figure 1) [27].
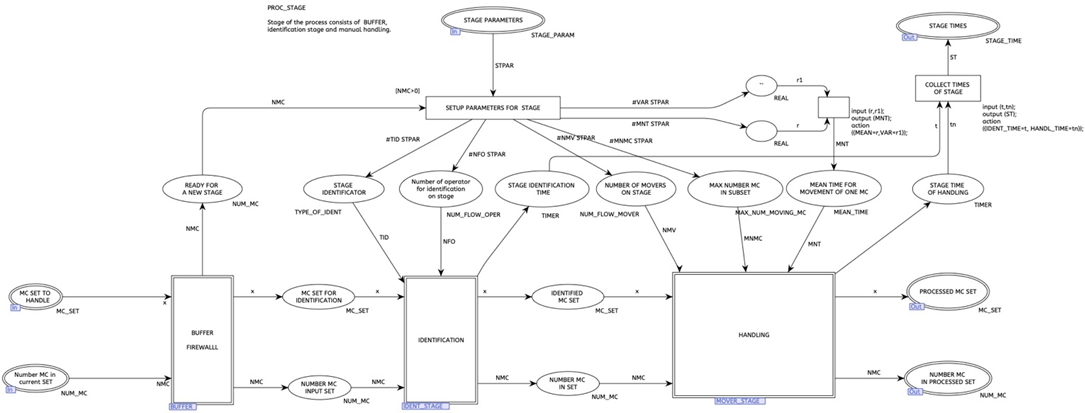
Fig. 1. Flight preparation process
The modeled process is represented as a sequence of stages - modules of the system, realizing the function of identification and the function of manual processing of mobile equipment.
In the model and the actual MOKE TCS system, the identification technologies are additional to the existing manual processing technology and do not change it in any way. There is no change in the number of personnel involved and their work routines. Visual identification is performed by the same personnel and is treated as a separate step. The use of any automated technologies leads to a decrease in identification time, increase in reliability and increase in the cost of implementation and use of specific hardware and software.
The applicability and compatibility matrices of identification technologies are used by the generation module to constrain the space of possible configurations and have the form shown in Figure 2.
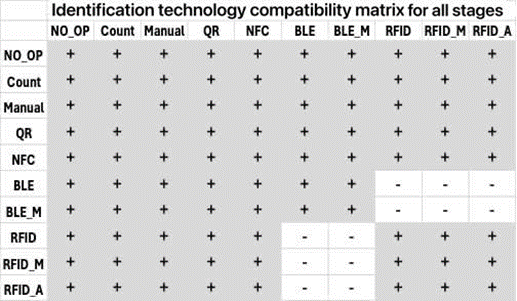
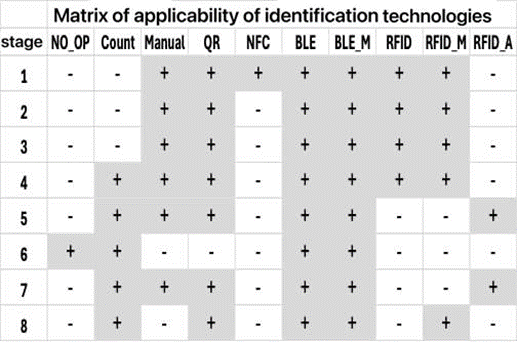
Fig. 2. Identification technology applicability and compatibility matrices.
The applied technologies can perform both group and individual identification of a MOKE unit. In case of group identification, the time delay is calculated once and applied to the entire group of mobile equipment.
Organizational constraints require the use of the same identification technology for the specified pairs of technological stages. In the model these are <2,3> and <5.7> stages.
2.2 Simulation model parameters
The time is determined by the probabilistic parameters of the identification method and the number of MOKE. The parameters are given by mean and variance and have different values for each identification method. The delay time is a random variable and is given by a normal distribution function.
The model has a stage parameter - the maximum number of MOKE units processed simultaneously. The specific number of MOKE units to be processed simultaneously is calculated by a random function of uniform distribution. In some stages, manual processing may not be performed. The model parameter (number of movers) equal to zero at a stage is interpreted by the model as the absence of manual processing stage.
3 Results and discussion
The generation module generates many possible configurations using a sequential search method. The set of possible configurations for a process with 8 steps has the capacity of 224 (16 777 216), However, taking into account organizational constraints reduces the power of the set of acceptable configurations to 28,800 (less than 215).
For each configuration, the coefficient of automation, the reliability of identification, and the implementation costs were calculated. The distribution of the number of configuration options based on given parameters was analyzed. Knowledge of these distributions allowed us to introduce into the model parameters of constraints that allowed modeling only for a selected group of configurations. This greatly simplified the modeling process, which was very time-consuming and sensitive to the number of iterations. The resulting distributions are shown in Figure 3 and Figure 4.
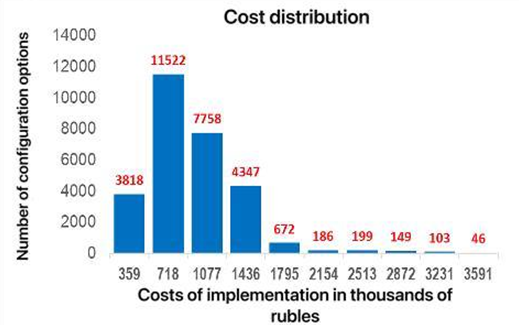
Fig. 3. Variation of the space of acceptable configurations depending on the level threshold

Fig. 4. Variation of the space of admissible configurations depending on the level threshold
The conducted analysis showed that the space of solutions, is discrete, submitted to clustering. The parameters of interest to us, necessary for solving the optimization problem (cost reduction and increasing the level of automation), have a limited set of values. Thus, the automation factor has 25 unique values and the cost level has 411. Configuration variants were divided into corresponding groups with the same automation ratio and within these groups were ordered by increasing cost level.
The automation threshold W introduced above can take values in the range from 1 to 4. The effect of the value of W on the distribution of the allowable configuration space is shown in Table 2 and Figure 5.

Fig. 5. Variation of the space of acceptable configurations depending on the confidence level threshold.
Modeling was performed at different values of the identification confidence level (Figure 6).

Fig. 6. Variation of the space of allowable configurations depending on the threshold of the automation level.
An increase in the confidence level leads, as expected, to a decrease in the total number of allowable configurations. At the same time, some areas with lower values of the automation factor do not include any configuration. There is a decrease in the range of cost level values in some areas (highlighted in gray in Table 2). We observed an increase in the lower cost area boundary values and a decrease in the upper boundary (highlighted in light brown in Table 2).
Table 2. Changing the space of acceptable configurations depending on the threshold of the automation level.
| Reliability | D≥0.9225 | D≥0.95 | D≥0.96 | D≥0.97 | D≥0.98 | D≥0.99 | |||||||
| No of configurations | 26910 | 25384 | 17883 | 11088 | 300 | ||||||||
| № | Ka | Level of costs | |||||||||||
| Min | Max | Min | Max | Min | Max | Min | Max | Min | Max | Min | Max | ||
| 1 | 1 | 0 | 0 | - | - | - | - | - | - | - | - | - | - |
| 2 | 1.125 | 46 | 200 | 46 | 46 | - | - | - | - | - | - | - | - |
| 3 | 1.25 | 46 | 246 | 46 | 246 | 86 | 246 | - | - | - | - | - | - |
| 4 | 1.375 | 46 | 95 | 46 | 905 | 46 | 445 | - | - | - | - | - | - |
| 5 | 1.5 | 0 | 1105 | 86 | 1105 | 86 | 1105 | 296 | 491 | - | - | - | - |
| 6 | 1.625 | 86 | 1151 | 86 | 1151 | 86 | 1151 | 86 | 1151 | - | - | - | - |
| 7 | 1.75 | 126 | 1271 | 126 | 1271 | 126 | 1271 | 126 | 1245 | 386 | 611 | - | - |
| 8 | 1.875 | 166 | 1311 | 166 | 1311 | 166 | 1311 | 166 | 1311 | 221 | 1271 | - | - |
| 9 | 2 | 140 | 2195 | 140 | 2195 | 140 | 2195 | 140 | 1411 | 221 | 1411 | - | - |
| 10 | 2.125 | 186 | 2345 | 186 | 2345 | 186 | 2345 | 186 | 1471 | 186 | 1451 | 306 | 691 |
| 11 | 2.25 | 175 | 2795 | 175 | 2795 | 175 | 2795 | 175 | 2795 | 175 | 1471 | 301 | 1351 |
| 12 | 2.375 | 221 | 2945 | 221 | 2945 | 221 | 2945 | 221 | 2945 | 221 | 2841 | 296 | 1491 |
| 13 | 2.5 | 175 | 2991 | 175 | 2991 | 175 | 2991 | 175 | 2991 | 175 | 2991 | 266 | 1511 |
| 14 | 2.625 | 221 | 3095 | 221 | 3095 | 221 | 3095 | 221 | 3095 | 221 | 3031 | 221 | 1651 |
| 15 | 2.75 | 210 | 3245 | 210 | 3245 | 210 | 3245 | 210 | 3245 | 210 | 3141 | 210 | 3041 |
| 16 | 2.875 | 256 | 3291 | 256 | 3291 | 256 | 3291 | 256 | 3291 | 256 | 3291 | 256 | 3081 |
| 17 | 3 | 245 | 3295 | 245 | 3295 | 245 | 3295 | 245 | 3295 | 245 | 3295 | 245 | 3191 |
| 18 | 3.125 | 386 | 3341 | 386 | 3341 | 386 | 3341 | 386 | 3341 | 386 | 3341 | 386 | 3341 |
| 19 | 3.25 | 375 | 3445 | 375 | 3445 | 375 | 3445 | 375 | 3445 | 375 | 3445 | 375 | 3341 |
| 20 | 3.375 | 421 | 3491 | 421 | 3491 | 421 | 3491 | 421 | 3491 | 421 | 3491 | 421 | 3491 |
| 21 | 3.5 | 410 | 3545 | 410 | 3545 | 410 | 3545 | 410 | 3545 | 410 | 3545 | 410 | 3445 |
| 22 | 3.625 | 575 | 3591 | 575 | 3591 | 575 | 3591 | 575 | 3591 | 575 | 3591 | 575 | 3591 |
| 23 | 3.75 | 575 | 3545 | 575 | 3545 | 575 | 3545 | 575 | 3545 | 575 | 3545 | 575 | 3445 |
| 24 | 3.875 | 740 | 1645 | 740 | 1645 | 740 | 1645 | 740 | 1645 | 740 | 1645 | 740 | 1645 |
| 25 | 4 | 905 | 1505 | 905 | 1505 | 905 | 1505 | 905 | 1505 | 905 | 1505 | 905 | 1505 |
3.1 Discussion
The article considers a class of cyber-physical systems for which, due to their specificity, it is impossible to use a single method of identification at all stages of the technological process to be automated. The proposed solution — using combinations of identification methods and technologies within one system, leads to the need to evaluate the possible options of combinations in order to find the optimal one. The formal formulation of the problem described in the article reduces the search for the optimal configuration (combination of identification technologies) to the solution of the multi-criteria optimization problem, and as a possible tool for its solution, the simulation model developed by the author is proposed. The created simulation model allows automating the process of generating the full space of admissible configurations and evaluating possible combinations of identification technologies according to the criteria described in the formal formulation of the optimization problem.
Simulation of the technological process allows checking the compliance of the configuration with time constraints. The obtained set of admissible configurations is limited by the threshold value of the level of identification reliability, grouped by the value of automation level and ordered within the group by increasing cost level. The created model is implemented as a software package, which is designed to generate variants, their evaluation by calculating parameters and simulation, analysis of the obtained solution space and search for local optimums.
Generate all possible configurations: construct an admissible set of configurations according to the given constraints; calculate the parameters for each configuration obtained; construct the distribution of the set of configurations according to the given parameters; set threshold values and constraints, in accordance with the formal formulation of the optimization problem; model the process execution for each configuration; evaluate the acceptability of the configuration based on the simulation results; output the simulation results to a file for further processing; construct a quasi-optimal set of configurations for selected values of model parameters.
The use of simulation allows to create a complete space of possible solutions, which provides analysis and evaluation of non-obvious, from the point of view of a human, options of configurations that would simply not be included by a human in the space of possible solutions.
Within the framework of the used toolkit, which is not designed for solving multi-criteria optimization problems, develop an algorithm and search for quasi-optimal solutions. In this way, the regions of Pareto-optimal solutions were obtained.
4 Conclusions
Given the operating conditions of cellular communication facilities in the airport area, it seems necessary to consider the possibility of organizing alternative data transmission channels, such as using LoRa technology.
The proposed approach, with some modifications, can be used to create automated systems for monitoring the functioning of complex agro-biotechnical objects.
Acknowledgements
The study was supported by the Russian Science Foundation Grant No. 24-19-00823, https://rscf.ru/project/24-19-00823/.
References
- Ronzhin, A.L. (2020). Application of radio frequency identification technology to build a system for controlling the turnover of on-board kitchen equipment. Voprosy radioelektroniki. Seriya: Tekhnika televideniya, 1, 3–10.
- Styskin, M.M., Stepanov, P.V., Zheltov, S.Yu., Sokolov, B.V., Ronzhin, A.L. (2022). Means of optical and radio frequency identification in the technological process of automated control of mobile on-board equipment circulation. Modeling, Optimization and Information Technology, 10(1), 36.
- Savinkova, S.A. (2021). Development of a method for tracking the movement of objects. Bulletin of Modern Research, 1-6(39), 28–36.
- Sokolova, V.D. (2022). Automatic identification of goods in logistics systems. Current Problems and Prospects for the Development of Radio Engineering and Information Communication Systems (Radioinfocom-2022), 688–693.
- Makarov, R.A. (2023). Recognition of freight container marking digits using the Faster-RCNN algorithm. Engineering journal of Don, 3(99), 203–213.
- Makarov, R.A. (2023). Freight container marking recognition algorithm using deep neural networks. Engineering journal of Don, 4(100), 225–237.
- Lyzganov, M.S. (2020). Bluetooth transport detector concept. Development of Science, National Innovation System and Technologies, 41–44.
- Gnidenko, A., Sobolevsky, V., Potriasaev, S., Sokolov, B. (2019). Methodology and integrated modeling technologies for synthesis of cyber-physical production systems modernization programs and plans. IFAC-PapersOnLine, 52(13), 642–647.
- Gupta, P., Krishna, C., Rajesh, R., Ananthakrishnan, A., Vishnuvardhan, A., Patel, S.S., Kapruan, C., Brahmbhatt, S., Kataray, T., Narayanan, D., Chadha, U., Alam, A., Selvaraj, S.K., Karthikeyan, B., Nagalakshmi, R., Chandramohan, V. (2022). Industrial internet of things in intelligent manufacturing: a review, approaches, opportunities, open challenges, and future directions. International Journal on Interactive Design and Manufacturing, https://doi.org/10.1007/s12008-022-01075-w
- Ali, R., Liu, R., He, Y., Nayyar, A., Qureshi, B. (2021). Systematic review of dynamic multi-object identification and localization: techniques and technologies. IEEE Access, 9, 122924 – 122950, https://doi.org/10.1109/ACCESS.2021.3108775
- M’hand, M.A., Boulmakoul, A., Badir, H., Lbath, A. (2019). A scalable real-time tracking and monitoring architecture for logistics and transport in RoRo terminals. Procedia Computer Science, 151, 218-225, https://doi.org/10.1016/j.procs.2019.04.032.
- Mohamed, I.S., Capitanelli, A., Mastrogiovanni, F., Rovetta, S., Zaccaria, R. (2020). Detection, localisation and tracking of pallets using machine learning techniques and 2D range data. Neural Computing and Applications, 32(13).
- Shi, S., Jiang, L., Deng, J., Wang, Z., Guo, C., Shi, J., Wang, X., Li, H. (2023). PV-RCNN++: Point-Voxel Feature Set Abstraction With Local Vector Representation for 3D Object Detection. International Journal of Computer Vision, 131(2).
- Chen, R., Li, W., Lan, K., Xiao, J., Wang, L., Lu, X. (2023). Fast adaptive binarization of QR code images for automatic sorting in logistics systems. Electronics (Switzerland), 12(2).
- Lorenc, A., Szarata, J., Czuba, M. (2023). Real-Time Location System (RTLS) Based on the Bluetooth Technology for Internal Logistics. Sustainability (Switzerland), 15(6).
- Potriasaev, S.A., Sokolov, B.V., Zhao, V.Yu.-D., Stepanov, P.V., Styskin, M.M. (2020). Features of using bluetooth low energy tags for identifying and determining the position of objects in the technological process of ground handling of civil aviation aircraft. Informatization and Communication, 6, 106-112
- Davydov, K.S., Astakhov, S.P. (2021). Use of RFID tags in production. Science and Technology: Current Issues, Achievements and Innovations, 44–48.
- Belaya, T.I., Kalikina, N.V. (2020). Automated monitoring system for transshipment operations in the cargo area of a seaport. Regional Informatics and Information Security, 122–125.
- Sheveleva, K.I., Shurinova, V.A., Ivaev, M.I. (2020). Features of RFID technology and its application in industrial warehouses. Naukosfera, 12-1, 181-185.
- Usama, M., Ramish, A. (2020). Towards a sustainable reverse logistics framework / typologies based on radio frequency identification (RFID). Operations and Supply Chain Management, 13(3).
- Want, R. (2006). An introduction to RFID technology. IEEE Pervasive Computing, 5(1).
- Unhelkar, B., Joshi, S., Sharma, M., Prakash, S., Mani, A.K., Prasad, M. (2022). Enhancing supply chain performance using RFID technology and decision support systems in the industry 4.0–A systematic literature review. International Journal of Information Management Data Insights, 2(2).
- Stepanov, P.V., Sokolov, B.V. (2021). Problems of using bluetooth tags with low power consumption for identifying and determining the position of objects. Proceedings of 2021 4th International Conference on Control in Technical Systems, CTS 2021.
- Stepanov, P.V. (2021). The methodology of using bluetooth technology to solve the problems of identifying and determining the position of objects. Informatization and Communication, (5), 97–104.
- Steshina, L., Glazyrin, A., Petukhov, I., Velev, D., Zlateva, P. (2023). Using Convolutional Neural Networks for Training Forest Machine Operators. Studies in Systems, Decision and Control, 457, 555–574, https://doi.org/10.1007/978-3-031-22938-1_38.
- Pavlov, A.N., Pavlov, D.A., Umarov, A.B., Gordeev, A.V. (2022). Method of structural-parametric synthesis of configuration multi-mode object. Informatics and Automation, 21(4), 812–845.
- Steshina, L., Petukhov, I., Glazyrin, A., Velev, D., Zlateva, P. (2020). The Simulation Modeling for Safe Use of Technical Systems (Example: Forest Machines). In 2020 International Conference on Computer, Electrical and Communication Engineering (pp. 1-4), https://doi.org/10.1109/ICCECE48148.2020.9223098.
Conflict of Interest Statement
There is no conflict of interest with respect to this study.
Author Contributions
Data Availability Statement
No external datasets were generated or analyzed in this study. The simulation code and model parameters not publicly available.
Supplementary Materials
There are no supplementary materials to include.